14-July-2011 – This post needs polishing!
14-Dec-2011 – Improved by repeating exercise at PCA.
01-Aug-2012 – I have created a script to create directory structure and openssl.cfg available at http://files.spectrumcs.net/public/Exchange-OpenSSL/
28-Aug-2012 – Look at http://www.sslshopper.com/csr-decoder.html and consider creating a web portal which will create the CA and Certs in one go.
Before diving in, remember to do the following
On Internet Name Servers
Create a DNS A record for remote.domain.co.uk pointing to customers WAN IP address.
Create a DNS A record for autodiscover.domain.co.uk pointing to customers WAN IP address.
On LAN Name Servers
Create a DNS A record for remote.domain.co.uk pointing to the customers server LAN IP address.
Create a DNS A record for autodiscover.domain.co.uk pointing to the customers server LAN IP address.
Internet Explorer
Download Win64 OpenSSL v1.0.1a Light for Windows from http://www.slproweb.com/products/Win32OpenSSL.html and install. Install to E:\OpenSSL-Win64.
Share the folder as OpenSSL. (Setup access to Full Control to Domain Admins only?)
Download openssl.cfg and place file in file in E:\OpenSSL-Win64\bin
Update openssl.cfg with customer specific information – ie Country, County, Town and Company name information as well as company abbreviation (used to describe the CA and the directories the files are stored in).
Explorer
Create the following directories
E:\OpenSSL-Win64\WHLB_CA
E:\OpenSSL-Win64\WHLB_CA\certs
E:\OpenSSL-Win64\WHLB_CA\crl
E:\OpenSSL-Win64\WHLB_CA\newcerts
E:\OpenSSL-Win64\WHLB_CA\private
E:\OpenSSL-Win64\WHLB_CA\requests
Create the following files
E:\OpenSSL-Win64\WHLB_CA\index.txt (completely blank file)
E:\OpenSSL-Win64\WHLB_CA\serial (must contain just “00” without the quotes)
| Full access | E:\OpenSSL-Win64\WHLB_CA | This Folder, subfolder and files | Domain Admins |
| Read access | E:\OpenSSL-Win64\WHLB_CA | This Folder, subfolder and files | WHLBSERV4\IIS_IUSRS (The IIS service) |
| Read access | E:\OpenSSL-Win64\WHLB_CA\index.html | This file ony | WHLBSERV4\IUSRS (The Anonymouse IIS services) |
| Read access | E:\OpenSSL-Win64\WHLB_CA\certs | This file ony | WHLBSERV4\IUSRS (The Anonymouse IIS services) |
| Read access | E:\OpenSSL-Win64\WHLB_CA\crl | This file ony | WHLBSERV4\IUSRS (The Anonymouse IIS services) |
IIS Manager
Add Virtual Directory, setting the alias as whlb-ca and the pyhsiscal path as E:\OpenSSL-Win64\WHLB_CA
On the WHLB-CA virtual directory go to the SSL Settings and untick “Require SSL”
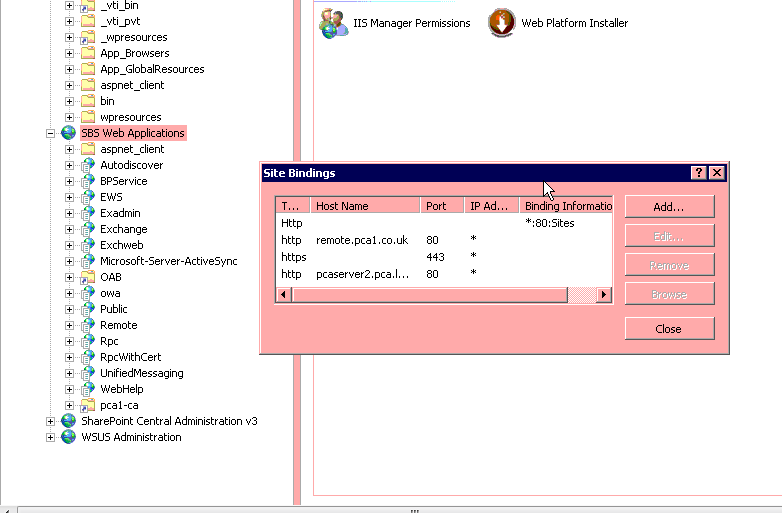
NOTE: If working on a SBS server you probably need to add the Virtual Directory to “SBS Web Applications” website. You may also need to alter the Websites bindings to include whlbserv4.wlhb.local
(screenshot from PCA)
At this point make sure you do not get any errors when browsing to http://internal-server-name/whlba-ca (note its HTTP not HTTPS, CRL must be accessible by HTTP).
Dos box
NOTE
I’ve started to received the following message from Chrome regarding our Self Signed SSL certs when using the commands below.
The site’s security certificate is signed using a weak signature algorithm!
There maybe a benefit to adding “-sha1” to the end of all / some commands.
cd e:\OpenSSL-Win6
set OPENSSL_CONF=E:\OpenSSL-Win64\bin\openssl.cfg (This sets the configuration location variable – Thanks to http://blog.webspheretools.com/2011/11/17/warning-cant-open-config-file-usrlocalsslopenssl-cnf/)
bin\openssl.exe genrsa -aes256 -out WHLB_CA\private\WHLB_CA.key -rand WHLB_CA\private\.rnd 2048
bin\openssl.exe req -new -x509 -days 18250 -key WHLB_CA\private\WHLB_CA.key -out WHLB_CA\certs\WHLB_CA.cer -rand WHLB_CA\private\.rnd
Enter pass phrase for pca1_CA\private\pca1_CA.key:
Loading ‘screen’ into random state – done
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [GB]:
State or Province Name (full name) [Hampshire]:
Locality Name (eg, city) [Andover]:
Organization Name (eg, company) [PCA1 (Certificate Authority)]:
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) [PCA1 (Certificate Authority)]:
Email Address []:certs@pca1.co.uk
bin\openssl.exe ca -gencrl -crldays 18250 -keyfile WHLB_CA\private\WHLB_CA.key -cert WHLB_CA\certs\WHLB_CA.cer -out WHLB_CA\crl\WHLB_CA.crl
Enter password.. no further information required….
Exchange Management Shell
execute the following cmdlets:
*** CAREFUL COPYING THESE LINES TO YOUR CLIPBOARD. THE QUOTATION MARKS GET CONVERTED TO UNICODE BY WORDPRESS. MAKE SURE AFTER YOU PASTE INTO EMS THEY’RE NORMAL QUOTES ***
$Data=New-ExchangeCertificate -GenerateRequest -KeySize 2048 -SubjectName “CN=remote.latchandbatchelor.co.uk , O=WHLB, L=Birmingham, ST=West Midlands, C=GB, OU=IT ” -DomainName whlbserv4, whlbserv4.whlb.local, remote.latchandbatchelor.co.uk, autodiscover.latchandbatchelor.co.uk -PrivateKeyExportable $True
Set-Content -path “E:\OpenSSL-Win64\WHLB_CA\requests\WHLBSERV4-EXCHANGE.csr” -Value $Data
Explorer / Notepad
Open “E:\OpenSSL-Win64\WHLB_CA\requests\WHLBSERV4-EXCHANGE.csr” and remove blank line at the end of the file. (After the last line of the CSR, but before the —–END NEW CERTIFICATE REQUEST—–)
Dos box
bin\openssl.exe ca -name ServerCA -policy policy_anything -in WHLB_CA\requests\WHLBSERV4-EXCHANGE.csr -out WHLB_CA\certs\WHLBSERV4-EXCHANGE-WRONGFORMAT.cer
bin\openssl x509 -outform der -in WHLB_CA\certs\WHLBSERV4-EXCHANGE-WRONGFORMAT.cer -out WHLB_CA\certs\WHLBSERV4-EXCHANGE.cer
Explorer
Double click WHLB_CA.cer and install into the “Trusted Root Certification Authorities” store.
* Might need to MMC, then Certificates and then install into Computers “Trusted Root Certification Authorities” store. Did it while testing and something and not sure if that is what made it work or not.
Install Certificate Authority by going into MMC, Adding Certificates snapin.
When prompted “My user account, service account or computer account”, select Computer Account. On the next screen select “Local Computer”.
Navigate to Certificates -> Trusted Root Certificate Authorities -> Certificates and import E:\OpenSSL\WHLB_CA\certs\WHLB_CA.cer into that store.
Exchange 2007 (Exchange 2010 below)
There doesn’t appear to be a GUI for importing the Certificate in Exchange 2007. Instead use the Exchange Management Shell.
Due to problems me and Tony had, check Certificate store before and after import to make sure somethings changed!
[PS] C:\Windows\system32>Get-ExchangeCertificate
Thumbprint Services Subject
---------- -------- -------
94885EAB1DC21F0115E6BB2BFAAC8AC6DCB07FC9 ..... CN=PCASERVER2.PCA.local
CDFCF1B9D458964409C75501450F907D4E5829F7 IP.WS CN=remote.pca1.co.uk
E60888C5A27432A5A2BF701DF5DCD8F02AC02B21 IP... E=postmaster@pca1.co.uk, CN=remote.pca1.co.uk, OU=StartCom Free Certificate Member, O=Persona Not Valid...
A5E446426A217453FAA265A2282B15C8A52E3FF9 ....S CN=Sites
49428658170A2E60E29C31DFC82A4671CD6E2F80 ..... CN=PCA-PCASERVER2-CA
89863B0D2E9094FFDCE11DB35B5DD62D98B5405C ..... CN=WMSvc-WIN-HMW1VHB4TJM
[PS] C:\Windows\system32>Import-ExchangeCertificate -Path E:\OpenSSL-Win64\PCA1_CA\certs\PCASERVER2-EXCHANGE.cer
Thumbprint Services Subject
---------- -------- -------
0F6E4712E00D31296B37AEBA21D163449294925F ..... CN=remote.pca1.co.uk, OU=IT, O=PCA, L=Andover, S=Hampshire, C=GB
[PS] C:\Windows\system32>Get-ExchangeCertificate
Thumbprint Services Subject
---------- -------- -------
0F6E4712E00D31296B37AEBA21D163449294925F ..... CN=remote.pca1.co.uk, OU=IT, O=PCA, L=Andover, S=Hampshire, C=GB
94885EAB1DC21F0115E6BB2BFAAC8AC6DCB07FC9 ..... CN=PCASERVER2.PCA.local
CDFCF1B9D458964409C75501450F907D4E5829F7 IP.WS CN=remote.pca1.co.uk
E60888C5A27432A5A2BF701DF5DCD8F02AC02B21 IP... E=postmaster@pca1.co.uk, CN=remote.pca1.co.uk, OU=StartCom Free Certificate Member, O=Persona Not Valid...
A5E446426A217453FAA265A2282B15C8A52E3FF9 ....S CN=Sites
49428658170A2E60E29C31DFC82A4671CD6E2F80 ..... CN=PCA-PCASERVER2-CA
89863B0D2E9094FFDCE11DB35B5DD62D98B5405C ..... CN=WMSvc-WIN-HMW1VHB4TJM
[PS] C:\Windows\system32>Enable-ExchangeCertificate -Thumbprint 0F6E4712E00D31296B37AEBA21D163449294925F -Services “IIS”
[PS] C:\Windows\system32>Enable-ExchangeCertificate -Thumbprint 0F6E4712E00D31296B37AEBA21D163449294925F -Services “SMTP”
Confirm
Overwrite existing default SMTP certificate, ‘CDFCF1B9D458964409C75501450F907D4E5829F7’ (expires 20/10/2011 09:01:10), with certificate
‘0F6E4712E00D31296B37AEBA21D163449294925F’ (expires 01/12/2061 15:52:09)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is “Y”): y
[PS] C:\Windows\system32>Enable-ExchangeCertificate -Thumbprint 0F6E4712E00D31296B37AEBA21D163449294925F -Services “POP”
[PS] C:\Windows\system32>Enable-ExchangeCertificate -Thumbprint 0F6E4712E00D31296B37AEBA21D163449294925F -Services “IMAP”
Check all services are using certificate (top line should now have IP.WS) :-
[PS] C:\Windows\system32>Get-ExchangeCertificate
Thumbprint Services Subject
---------- -------- -------
0F6E4712E00D31296B37AEBA21D163449294925F IP.WS CN=remote.pca1.co.uk, OU=IT, O=PCA, L=Andover, S=Hampshire, C=GB
94885EAB1DC21F0115E6BB2BFAAC8AC6DCB07FC9 ..... CN=PCASERVER2.PCA.local
CDFCF1B9D458964409C75501450F907D4E5829F7 IP.WS CN=remote.pca1.co.uk
E60888C5A27432A5A2BF701DF5DCD8F02AC02B21 IP... E=postmaster@pca1.co.uk, CN=remote.pca1.co.uk, OU=StartCom Free Certificate Member, O=Persona Not Valid...
A5E446426A217453FAA265A2282B15C8A52E3FF9 ....S CN=Sites
49428658170A2E60E29C31DFC82A4671CD6E2F80 ..... CN=PCA-PCASERVER2-CA
89863B0D2E9094FFDCE11DB35B5DD62D98B5405C ..... CN=WMSvc-WIN-HMW1VHB4TJM
Exchange Management Console (2010) (Exchange 2007 above)
Navigate to Microsoft Exchange -> Microsoft Exchange on Premises (whlbserv4.whlb.local) -> Server Configuration
Exchange Certifictes (Bottom Panel)
Right click certificate with “This is a pending certificate siging request (CSR)” and click “Complete pending request”, browse to E:\OpenSSL-Win64\WHLB_CA\certs\WHLBSERV4-EXCHANGE.cer
Right click certificate the same certificate and click “Assign services to the certificate”, click IMAP, POP, SMTP and IIS services. When asked if you want to enforce SSL, click yes
IIS Manager
On the WHLB-CA virtual directory go to the SSL Settings and untick “Require SSL” (already done one, but required again after clicking Yes above 😉
Distributing your Certificate Authority
You can use Group Policy to distribute your certificate authority to the workstations within you domain. You can also add the Certificate Authority manually (to remote workstations, mobile phones etc) by going to http://remote.example.com/ca-folder/certs/cafilename.
* In my experience it is not possible to import a CA into an non-rooted Android Phone.
eg http://remote.stkare.co.uk/svl-ca/certs/SVL_CA.cer
To add a trusted root certification authority to a Group Policy object
- Open the Group Policy object (GPO) that you want to edit.
- In the console tree, click Trusted Root Certification Authorities.Where?
- Policy Object Name/Computer Configuration/Windows Settings/Security Settings/Public Key Policies/Trusted Root Certification Authorities
- On the Action menu, point to All Tasks, and then click Import.This starts the Certificate Import Wizard, which guides you through the process of importing a root certificate and installing it as a trusted root certification authority (CA) for this GPO.
Something to document
A handy powershell command
Test-OutlookWebServices | fl (fl formats it!)